CREST Summer Scholarships
With the vision of building a talent pipeline of software security engineers, each year, CREST selects a highly talented group of young computer science undergraduates and master's students and offers them scholarships to participate in the CREST summer research program. The program aimed to enable scholarship holders to gain valuable knowledge and skills in engineering software systems supporting cybersecurity by leveraging artificial intelligence (AI), big data technologies, and security systems. Motivated by the CREST - the Centre for Research on Engineering Software Technologies team's commitment to helping build a talent pipeline of software security, this initiative has been highly appreciated by all involved, particularly by the students.
This program also provided several postdocs and PhD students at CREST with the opportunity of gaining valuable experiences in leading small-scale engineering projects focused on supporting the security of the software digital systems related to our large-scale R&D projects supported by our industry and government partners, such as National Australia Bank - Nab, ActewAGL, Jemena, Cisco, Tata Consultancy Services, Defence SA, Defence Science and Technology (DST), QuintessenceLabs and SA Health.
This initiative also enabled us to test the scalability of our support infrastructure and mentoring practices for real-world projects. Based on the observations/experiences and feedback, we are working on the next phase of this initiative. Please let us know if you would like to know more about any particular aspect of our summer program.
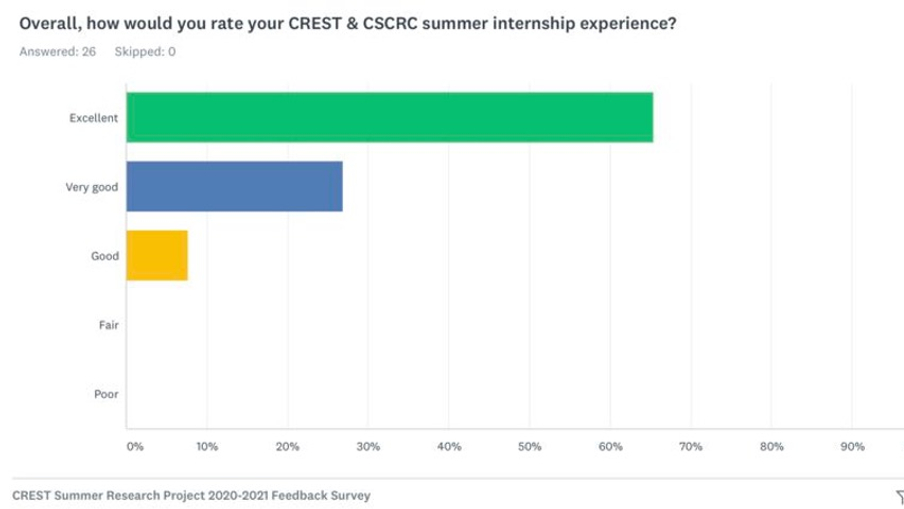
Feedback from the CREST Summer Scholarship program (2020-2021 and 2021-2022)
“First of all, I would like to express my gratitude for being a part of such a wonderful program. The communication with the organizers was seamless, and the meaningful discussions with my fellow scholars were inspiring. The diverse perspectives provided by clients and supervisors gave me a different way of thinking about the problems we were solving and allowed me to provide unique solutions. The experience I gained during the summer scholarship have been invaluable in my career development. It helped me to get familiar with the working environment, and I got help from my supervisors whenever I needed it. I am confident that the experience I gained during the scholarship will continue to benefit me in the future.”
“It was my first time working on a research project in data science/cyber security domain. Learning to read and assimilate information from research papers, understanding the topic and designing the methodology to answer the research questions were my main takeaways. I also got exposure to OpenStack cloud, simulating exfiltration attacks, which added to my skill set. This experience helped me in my interviews to showcase my technical as well as project execution skills. The project was also found by my interviewer as relevant to the work the company is doing. I have also made connections during this time which has broadened my network. I believe the internship duration and the way it was implemented worked very well for me.”
“Throughout the program, I gained practical experience in advanced machine and deep learning techniques, which significantly enhanced my skills and knowledge in this field. In addition, I had the opportunity to work alongside accomplished professionals who provided me with invaluable guidance and mentorship that had a profound impact on shaping my research interests and approach. Furthermore, the summer scholarship program allowed me to connect and network with other scholars and professionals in the industry, which enabled me to keep apprised of the latest trends and technologies. This has been especially beneficial in my current role as a PhD researcher.”
“My experience while working at CREST was an amazing one. Firstly I got an opportunity to work on - Comparison of DL methods for managing security patches projects, which still helps me in day-to-day ML projects. Tasks like reading and discussing a research paper, queuing tasks on Phoenix using Linux commands, experimenting with different metrics, etc helped me to broaden my technical skills, which are still relevant in my current work.”
Our interns and projects from the CREST summer scholarship program in 2021-2022
Human security dashboard
The exponential growth of technological advancements has led to significant growth of security threats and risks. No matter how small they are, businesses now need to be aware of and consciously apply security measures at every level. Despite the many countermeasures, technologies, and solutions to mitigate security breaches and related threats, successful security attacks are still on the rise. Technology alone cannot be considered a comprehensive solution to all sophisticated organisational security threats; the people in the organisations are actually the primary and the weakest line of defence.
This project aims to design a human security dashboard using the existing Cyber Common Operating Picture (CCOP) platform and infrastructure. This human security dashboard will visualise various metrics covering various aspects of human security, including phishing and security training and engagement. The human security dashboard will allow organisations to keep a close eye on how the security risk of an organisation changes due to employees in the organisation and take proactive countermeasures swiftly.
Supervised by: Asangi Jayatilaka and Ali Babar
Minhaj Ahmed
Minhaj Ahmed is a second year Bachelor of Computer Science (Advanced) student at The University of Adelaide. Minhaj has received a scholarship on his admission at The University of Adelaide based on academic merit. His fascination towards research has propelled Minhaj to get involved in project works, and he is working on a project which aims at designing a human security dashboard which would visualise various metrics covering various aspects of human security, including phishing, security training and engagement. The research is being supervised by Dr Asangi Jayatilaka and Professor Ali Babar. Minhaj is excited to leverage on the opportunity to explore new techniques and use this learning experience as a driving force for his future career.
An Empirical Analysis of Pre- and Post-Release Vulnerabilitie
Vulnerability mitigation can occur at many stages of the Software Development Lifecycle (SDL). Importantly, there are two main categories of vulnerabilities based on the stage at which they are detected: pre-release vulnerabilities that are identified internally during testing and development, and post-release vulnerabilities that escaped the testing phase and have been identified in deployed products. There is an important distinction between these two categories, as post-release vulnerabilities are exposed to the user and potential malicious actors, resulting in potential security impacts and devastating consequences. Hence, ideally all vulnerabilities should be identified pre-release.
This naturally poses the question as to why these vulnerabilities have been detected at different stages of the SDL; why do some vulnerabilities escape the testing phase whereas others do not. If the characteristics of these vulnerabilities differ, it is also imperative that we garner an understanding of the consequences on software testing and debugging, so that we can develop better detection methods and more targeted code analysis techniques.
In this project, we will use quantitative and regression analysis to derive insights into different categories of vulnerabilities. Furthermore, we will investigate how differences in these vulnerabilities can impact downstream tasks, such as predictive modelling.
Supervised by: Roland Croft and Ali Babar
Pitawelayalage Dasun Pitawela
I am Dileepa, a student reading for Master of Data Science. I completed my BSc. (Hons). at the University of Moratuwa, Sri Lanka and worked for about 2.5 years as a Software Engineer in the industry. It is a great pleasure to announce that I’ve been awarded the CREST summer research scholarship for the second consecutive year. During this program, I get to work in a cyber security related research project that has an industry level impact. It indeed helps me to level up my software engineering skills as well as research skills. Apart from academics, I volunteer as an International Peer Mentor in International Student Support, as a Volunteer Ambassador in the faculty of ECMS and as an active member in the University of Adelaide chapter of Golden Key international student honour society which recognises top 15% students of the university.
Evaluation of Benchmarking Dataset for Data Exfiltration
Data exfiltration is the process of retrieving, copying, and/or transferring data without authorization. According to Verizon Breach Report, a total of 157,525 data exfiltration/breach incidents have been reported in 2020. In order to detect, prevent, and investigate data exfiltration, several data exfiltration countermeasures have been recently proposed. However, evaluating these countermeasures is a challenge. This is because of the unavailability of a benchmark dataset to rigorously evaluate these countermeasures with respect to various metrics such as accuracy, response time, and scalability. Previously, we have created a benchmarking dataset for data exfiltration.
In this work, we aim to evaluate how good/bad is the dataset. We plan to evaluate the dataset to answer the following questions – (i) Whether or not the testbed used for generating the dataset represents a real-world scenario? (ii) How accurately ML/DL approaches classify the instances in the dataset intro respective classes? (iii) Whether or not the datasets is labelled correctly and in a reliable manner? (iv) Whether or not the data is captured in its entirety? (v) Is the dataset skewed significantly towards one particular class (e.g., benign)? (vi) Whether or not sharing the dataset publicly violates any privacy or ethical concerns?
Supervised by: Faheem Ullah and Ali Babar
Mythri Ramadas Kadaba
I am Mythri Ramadas Kadaba, a Masters of Datascience student at the University of Adelaide. I have completed my Bachelor in engineering from Bangalore, India. I have worked for over 5 years in database administration and data mining support projects in India and UK. I enjoy working with data and making sense of it, while using machine learning techniques to enrich the information extraction.
Metadata augmentation of Combat System Maps
Combat Management Systems are used to empower naval platforms throughout the world in the execution of their missions. An important feature of a Combat Management System is the ability to visualize a situation and the environment in which it occurs. A 'Map Server' provides reference information to components, such as user interfaces, that support building a cohesive and consistent picture of the evolving situation for all consumers of the information.
This project aims to build a Map Server of tomorrow that will provide an enhanced map to the end-users. The Map Server will be built by combining the rich contextual data, providing both a graphical picture of what things are at a location, together with more descriptive data that give a richer picture of each entity's capabilities and characteristics.
The expected outcome of this project is a metadata-enabled Combat Management Systems 'Map Server' that incorporates the Graphical Information System (GIS). The developed Map Server should provide a deeper level of details about locations or areas, which will be used to conduct a range of analyses and experiments. The effectiveness of the Map Server will be evaluated in manipulating and visualizing the information of the Map Server over traditional maps (augmented with reference information metadata concepts).
Supervised by: Ali Babar, Aufeef Chauhan and Tim Priest
Ruixuan Zou
I am a current MSc Data Science student at the University of Adelaide, currently in the second year of my MSc career. My work background is in data analysis in business investment, and my main research interests at university are in computer vision and pattern recognition, with a focus on unsupervised machine learning directions.
Distributed Decision Making in a Crisis: How can AI help the Emergency Services
Emergency services in Australia include Police, Fire (both metropolitan and country), Coast Guard, Surf Lifesaving, Paramedics, State Emergency Service and more. These services regularly work together as heterogeneous teams to address many complex situations, utilising a wide range of capabilities and technologies across a diverse range of environments and scenarios. The individual doctrine, training, policies and governance of these services impacts the way in which the services work together and how communication is handled for human-human teams, human-machine teams and, increasingly, machine-machine teams.
In responding to any emergency (and potentially life-threatening situation) decisions on how to respond are made quickly and with information that ranges in content and quality; leading to potential uncertainty, ambiguity and delay in response. The varying platform capabilities, roles and operator skill levels across heterogeneous information systems of the emergency services add to the response-complexity problem and ability to optimise response planning. The underlying technologies to support emergency service operations must therefore be robust, resilient and adaptive to allow the 'who, what, where and when' for agile response planning across the heterogeneous capability environment.
This project, hosted by the Human and Autonomous Decision Systems group at DST, will investigate methods and technologies that could be employed and harnessed to produce solutions to issues such as optimised distributed decision making faced by emergency services and other domains. We are open to solutions, but this project could involve the use of Artificial Intelligence (AI), Machine-Learning (ML), micro-service architectures and self-aware systems or a combination of innovative techniques. Whatever the solution, your goal is to optimise the application of emergency service capabilities in response to critical situations.
Supervised by: Ali Babar, Aufeef Chauhan and Tim Priest
Yankun Chen
I am Yankun Chen, studying for a double-degree: Bachelor of Mathematics and Computer Science with Bachelor of Finance. This is my fourth year of study, and I will graduate in June 2022. Before starting to study my bachelor in University of Adelaide, I had worked for several years in three companies in China and in Singapore. I was awarded Master and Bachelor degrees in Electrical engineering in Beijing Jiaotong University.